
Account Security
Complete Account Security, From First Click to Final Transaction
Complete Account Security, From First Click to Final Transaction
Protect every touchpoint in the customer journey from browsing, account creation, login, details change, checkout and payment. Configure new journeys in real time, without engineering resource.
Book a demo
Current Account Security Challenges
Fraud and abuse targeting customer accounts is more complex and fraudsters more successful. Fraud-as-a-service providers use AI to scale and enhance the efficacy of attacks, pivoting to new touchpoints and unprotected endpoints in minutes. Businesses are often hamstrung by legacy solutions that are cumbersome to manage, hard to update, and fall foul of consumer privacy preferences.
Point Solution Siloes
Legacy fraud solutions protect key moments in the customer journey, such as logins or payments, but often lack the context and visibility of the entire customer journey. Fraudsters use this to their advantage by exploiting new touchpoints and unprotected API endpoints.
AI-Facilitated Attacks
Generative AI is being utilized by fraudsters to enhance their tactics and increase their likelihood of success. Use cases include email, message and image creation for social engineering, chatbots, deepfakes, lists of password combinations for credential stuffing attacks, code creation and adversarial AI.
API Sprawl
As digital businesses grow, APIs are increasingly adopted to enable interoperability between different systems, applications, and services. This creates a larger attack surface for fraudsters to exploit, and requires complete visbility, logging and monitoring to protect new or exposed API endpoints.
Advanced AI Bots
Unlike traditional bots that perform rapid, high-volume actions, Advanced AI bots to mimic human behavior. This makes them harder to detect via rate limits or legacy defenses, and more likely to infiltrate user accounts.
Stolen & Spoofed Identities
Stolen and spoofed identities are used to mimic legitimate users and exploit weaknesses in authentication and verification processes. This data is often combined with social engineering to divulge one-time passcodes or missing login data.
Scams & Social Engineering
Scams encourage a trusted customer into making a booking or payment directly to a fraudster. They use extremely effective tactics to convince customers they are buying a legitimate product or service, often using generative AI to increase success.
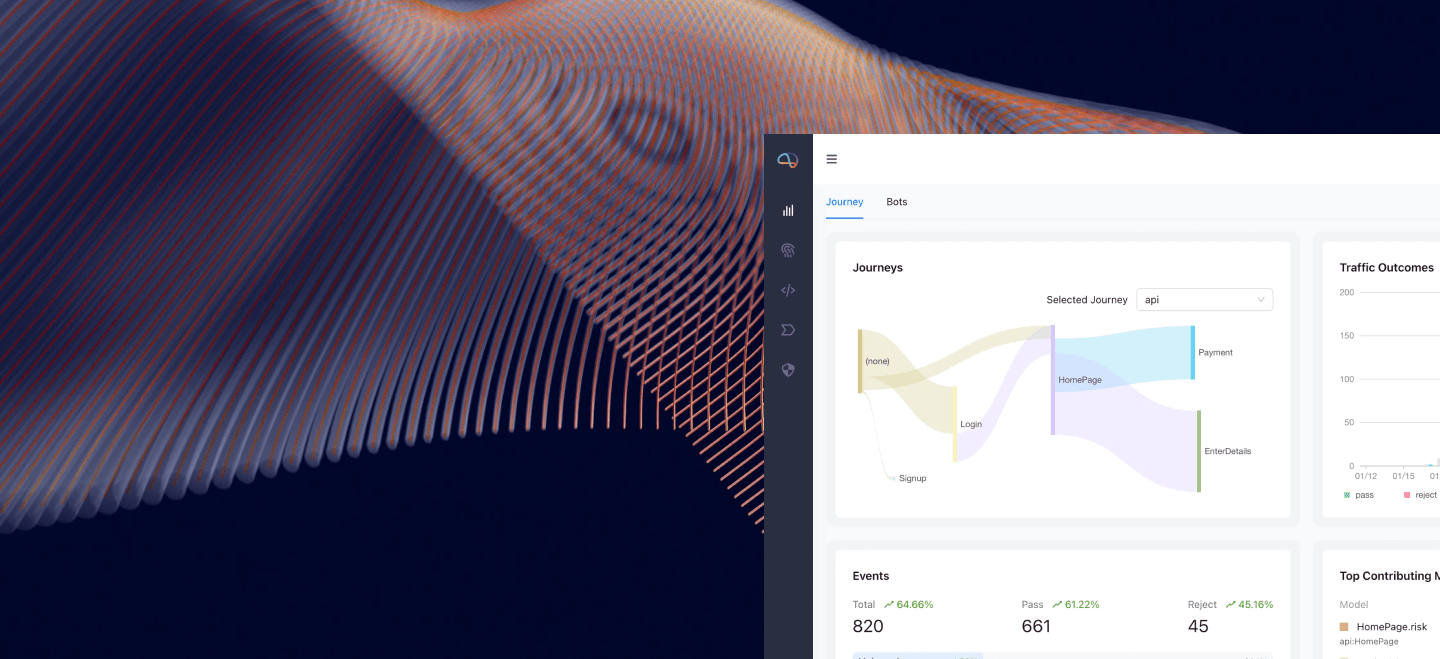
Customer Journey Protection
Understand true user intent, with full visibility of fraud and risk intelligence across security, fraud and customer experience teams.

- Automated bot attacks are becoming more intelligent, bypassing rate control measures and Captchas to infiltrate customer accounts.
- Harness intelligence from upstream behaviors to make more informed decisions at payment, and feedback bot behaviors from downstream interactions to enhance risk decisions upstream.
- Take action by triggering a step-up, blocking access or dynamically throttling traffic to slow down bots.
Protect Every Touchpoint in the Customer Journey with Unified Analytics and Actions
Identify cross-channel, fast-moving and highly adaptive account security threats. Unify siloed systems and disconnected signals to remove blind spots that attackers exploit.


Whitepaper
Account Security Whitepaper - Continuous Protection for the Digital Customer Journey
The Darwinium team showcased a profound understanding of our requirements, offering innovative solutions to help us reach our objectives. They are not only knowledgeable but also bring a creative approach to problem-solving. The platform's flexibility is particularly impressive, allowing us to meet the unique needs of our business and clients.

Egle Nartautaite
Global Fraud at Pitney Bowes

Get in touch
Talk to Us About Account Security
Looking to enhance your defenses against account takeovers, credential stuffing, or social engineering attacks? Our team is here to help.
Contact us
Frequently Asked Questions

Whitepaper