
The Darwinium Platform
Uniting Real-Time Analytics with Decisions and Actions
Uniting Real-Time Analytics with Decisions and Actions
Fraud Intelligence & Analytics
Continuous profiling of user behavior across every digital interaction. Future-proofed device and behavioral profiling with industry-first digital signatures.
Make Decisions, Take Actions
The decision platform orchestrates both decisions and actions across customer journeys. Plug & play integrations play nicely in existing stack.
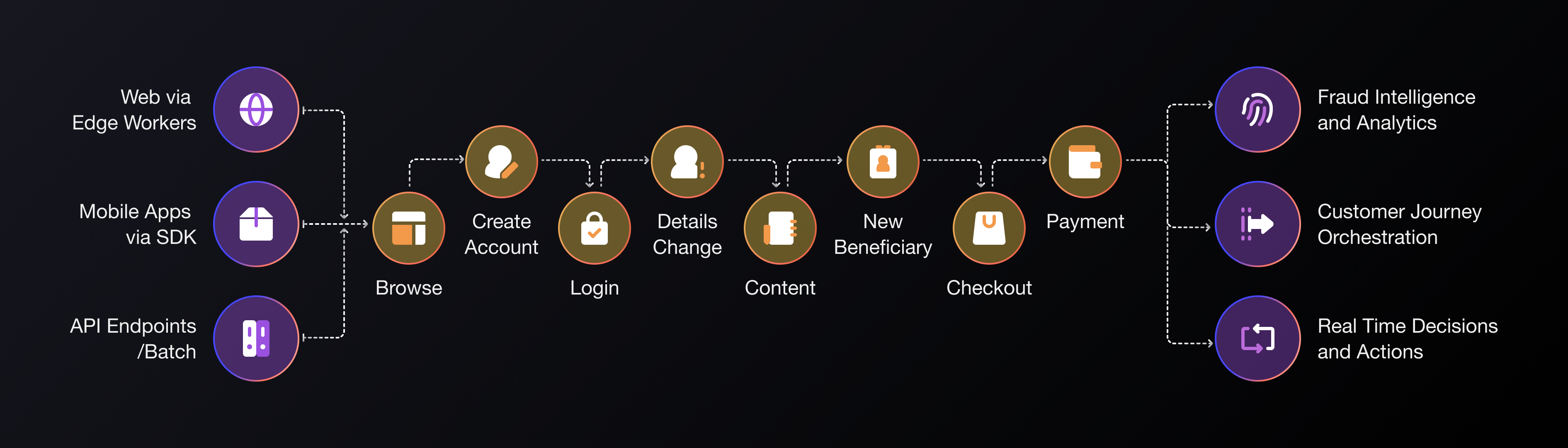
Flexible Deployment, Everywhere
Deploy on the edge via your CDN for full visibility across the customer journey, on critical webpages, on mobile via a lightweight SDK and on API endpoints.
Before Darwinium
After Darwinium
You see fragments of a user's behavior, each interaction telling a different story.
You see the full picture. Connected behaviors, unified decisions, one seamless view.
Fraud Intelligence & Analytics Across Every Customer Journey
Adversaries are exploiting business siloes and gaps in fraud intelligence. Darwinium removes these vulnerabilities with a single view of customer behavior across every digital journey, with fine-grained analytics that detect high-risk scenarios that other solutions miss.
Darwinium unites data and intelligence across the entire customer journey, piecing together user behavior over time, and across every digital touchpoint. Compare a user's behavior against their previous interactions on your site or against a cohort of users' interactions. Use those to form risk signals for more accurate decisioning.
Uncovering Hidden Fraud in Minutes with Darwinium
Darwinium helped us identify fraud on multiple seller accounts that we hadn’t identified before. This is a really great example of value darwinium has enabling the traceability and exploration of a threat or issue through to solution in a matter of minutes.

Nikolaus Brauer
Software Architect

Investigations
Give your fraud and risk teams the tools they need to deep-dive into suspicious activity across the shopper journey. Darwinium’s investigation tools are designed for business users, analysts, and data scientists to quickly uncover fraudulent behavior, like promo abuse, account takeovers, or bot-driven checkout attacks, with clarity and precision.
Adapt Faster than Release Cycles with Built-In Decisions and Actions
Adapt Faster than Release Cycles with Built-In Decisions and Actions
Move seamlessly from analytics to action, with real-time customer journey orchestration - featuring an integrated decision platform, plug and play third-party integrations and dynamic, tailored remediation.
Decision and Action in Real Time
Define journey and data mapping behaviors from within the Darwinium portal. Remove reliance on engineering resource to make code changes to take action. Train, test and deploy machine learning models without risk, removing reliance on black-box scores.
Integrated Decision Platform
Journeys, features, rulesets and models are configurable by no-code GUIs, low-code or full code options to suit all user groups. Use either a drag and drop interface, or a developer-friendly VSCode-based integrated development environment (IDE).
Incident Management
Providing additional context and visibility of customer interactions to both security and fraud teams while speeding up the triage, investigation and remediation of threats. Smart grouping of related events. Prioritize incidents based on what matters most to your team. Custom close actions connect directly with downstream systems. Built-in time tracking and incident metrics.
Feature Library
Powerful, extensible, native features generate in real-time and track statistical aggregates and risky behaviors over custom lookback timeframes.
Rule Engine
Install best practice signals from templates to solve particular use cases, then adapt and customize according to business priorities.
Model Execution
Bring your own advanced models in PMML format, using your own tools and pipelines. Productionize them instantly.
Conditional Orchestration
Darwinium is never a bottle-neck for data or actions. Call out to other party providers using templates in the Darwinium marketplace, or easily specify and consume custom APIs. Optimize decisions and step-ups based on risk.
Dynamic, Tailored Remediation
Add / reduce friction or block transactions based on risk. Inject dynamic, tailored messaging during a suspected scam journey. Call an API to do an additional authentication check. Terminate a session. Offer a VIP bonus to incentivise basket completion. Remove the operational headache between making decisions and taking action.
Flexible Deployment Across Your Digital Estate, with In-Built Privacy-by-Design
Comprehensive deployment options cover your content delivery network (CDN), web, apps and APIs, removing pressure on IT resource and decoupling remediation from release cycles. Darwinium gives customers the option to move data classification, encryption and anonymization to the perimeter edge. Retain full control of sensitive data, with less exposure to risk. Darwinium uses a fully anonymized version of this data that can be processed globally for security and fraud prevention purposes. The original data is not recoverable.
On the Edge
Dynamically adapt to new areas of attack and use cases without needing engineering effort, using content delivery network (CDN) infrastructure.
On Webpages
Designed for single-page applications and for core risk points. JavaScript tags, first-party profiling, blocker protection, no missing data.
On Mobile
Lightweight SDK for Android and iOS. Benefit from leveraging native profiling and consistency of decisioning controls between Web and Mobile.
API Endpoints
Protect integrity of API endpoints. Wildcarded monitoring of routes with sequence, discovery and parameter aware controls to detect abuse.
Get in Touch